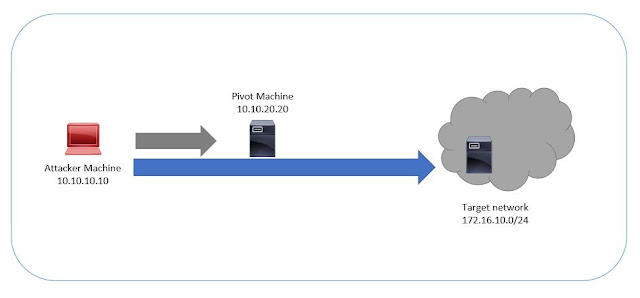
Pivoting is a technique used during Pentesting. The attacker gain access on one of the remote machine in the target network segment and use that machine to move around another network.
Note that the older versions of metasploit supports MSF scripts but the latest version (metasploit 6.x) doesn't support it. So lets see how to perform pivoting using the newer versions of Metasploit. For the illustration, i assume that the attacker has been gained the access to one of the remote machine and now he needs to move around.
After establishing a meterpreter shell, background it. Since msfscripts are deprecated, we should use the post/multi/manage/autoroute module.
msf> use post/multi/manage/autoroute
-set the SUBNET (new network range)
-set the SESSION (meterpreter session)
-run
You may see the following message after executing the module.
[!] SESSION may not be compatible with this module (incompatible session platform: windows)
[*] Running module against PC-1
[*] Adding a route to 172.16.10.0/255.255.255.0...
[+] Route added to subnet 172.16.10.0/255.255.255.0.
[*] Post module execution completed
Alternatively, you can add the route manually, using the following command from msfconsole.
route add 172.16.10.0/24 1
-where 1 is the meterpreter session.
Now the route has been added successfully. Lets do a port-scan of the remote network (172.16.10.0/24)
To run a port scan of the target network using metasploit,
use auxiliary/scanner/portscan/tcp
set RHOSTS // Specify the network
set THREADS //Specify the threads
set PORTS //Specify the ports to scan
run
If you would like to know how to pivot through different network, read this post.