In order to create an incident automatically by the Cortex XSOAR, you need to configure integrations with your 3rd-party products such as SIEM, ticketing tools, logs servers, network devices, EDR etc to start fetching events. Then you have to determine how the events ingested from those integrations will be classified as incidents. This is known as Classification Mapping. Then you create the pre-processing rules that enable you to perform certain actions on incidents as they are ingested into Cortex XSOAR. The entire process from an incident getting created till to the Closure/Archiving is explained below.
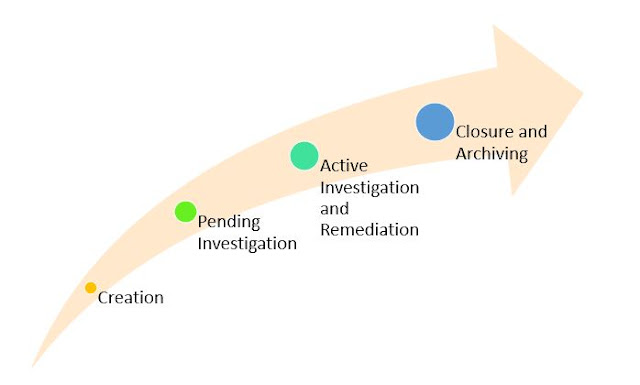
The lifecycle of an XSOAR managed incident consists of five phases:
- Creation
- Pending investigation
- Active investigation and remediation
- Closure and archiving.
Creation
A detected security event becomes an incident that Cortex XSOAR manages when the incident record for the event is created within Cortex XSOAR. The information (such as logs, alerts, events etc) from the devices/solutions (such as SIEM, ticketing tools, monitoring tools, network devices etc) can be ingested in to Cortex XSOAR and the incident records in Cortex XSOAR will be created automatically. You can also generate Cortex XSOAR incidents by using a remote REST API call to the Cortex XSOAR system or by manually entering the incidents in the Cortex XSOAR web interface.
Pending Investigation
Every Cortex XSOAR incident is matched to an incident type. The default type for a new incident is “unclassified.” An incident type can be associated with a predefined playbook. If an incident is matched to a type with no assigned playbook and the type option “Run playbook automatically” is not selected, Cortex XSOAR assigns the “pending” status to the incident.
Active Investigation and Remediation
Cortex XSOAR assigns the “active” status to an incident when investigative action on the incident starts. If the incident is matched to a type with a playbook defined and the type option “Run playbook automatically” is selected, the incident will proceed to the “active” status automatically. Otherwise, you start an investigation by manually navigating to the incident’s details page.
Closure and Archiving
Incidents can be closed automatically or via a manual selection process. After closure, the final stage in the lifecycle of an incident is archiving. Archiving is optional relative to the Cortex XSOAR storage capacity and the accumulation rate of incident data.
Read more posts on Palo Alto Cortex XSOAR here. 👆
Ref: docs.paloaltonetworks.com and beacon