On 23rd March 2018, the latest version of TLS ,which is TLS 1.3 has been approved by the IETF. There are a considerable number of improvements and differences in TLS version 1.3 over 1.2. Now the developers need to implement this version in to their products and the actual roll out can be expected soon.
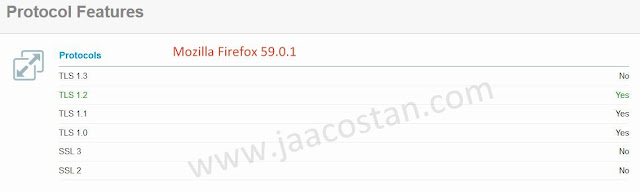
Right now, I'm having a Mozilla Firefox version 59.0.1 and by default the TLS1.3 is not yet enabled.
But as per some tech forums, the browser does support TLSv1.3 though its not enabled by default. There are some tips available over internet on enabling TLSv1.3 manually but i'm not going to discuss that here.
On TLS version 1.3,one of the major improvement is the speed.
Those who need a revision on SSL handshake process, can refer to my older post.
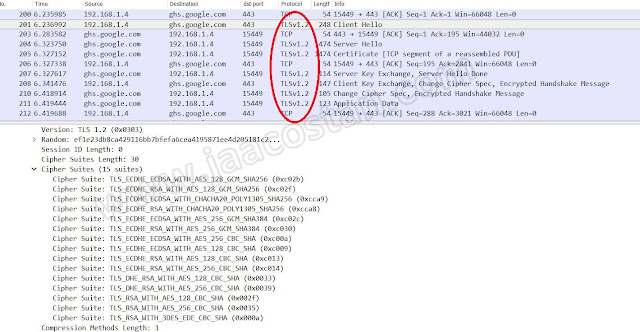
So the handshake process in TLS1.2 have more packet exchanges.
The whole handshake process in TLS 1.3 will be now concluded in just 3 exchanges.
But basically the concept is same. Client starts with HELLO, Server responds with its HELLO. then session key exchange.The same process will remain the same for TLSv1.3 version as well but the number of round trip exchanges will be reduced to 3 by eliminating the negotiation on the kind of encryption to use. Instead, the initial connection is a statement from the client mentions what methods and modes i am going to use and server accepts it and respond, that speed up the handshake process. This also helps to eliminate the downgrade attack vector.
A few other major differences between TLS 1.2 and TLS 1.3 are mentioned below.
1)The list of supported symmetric algorithms has been pruned of all algorithms that are considered legacy. Those that remain all use Authenticated Encryption with Associated Data (AEAD) algorithms.The ciphersuite concept has been changed to separate the authentication and key exchange mechanisms from the record protection algorithm (including secret key length) and a hash to be used with the key derivation function and HMAC.A few other major differences between TLS 1.2 and TLS 1.3 are mentioned below.
AEAD is the only encryption approach without any known weaknesses.AEAD suites provide strong authentication, key exchange, forward secrecy, and encryption of at least 128 bits. TLS 1.3 supports only AEAD suites. SSL labs started applying scoring penalty consideration for websites that does not having AEAD support.
2) A 0-RTT mode was added, saving a round-trip at connection setup for some application data, at the cost of certain security properties.
It means that if the client has connected to the server before, TLS 1.3 permits a zero-round trip handshake.This is done by storing secret information such as session ID of the previous sessions and using them when both parties connect with each other in future.
3)Static RSA and Diffie-Hellman cipher suites have been removed; all public-key based key exchange mechanisms now provide forward secrecy.
The SSL labs has already implemented a Penalty for not using forward secrecy in its scoring system ,if the website doesn't implement PFS.
4)All handshake messages after the ServerHello are now encrypted.The newly introduced EncryptedExtension message allows various extensions previously sent in clear in the ServerHello to also enjoy confidentiality protection from active attackers.
Also TLSv1.3 discontinued the support for obsolete ciphers and algorithms. That list includes the following major cryptographic standards/algorithms.
4)All handshake messages after the ServerHello are now encrypted.The newly introduced EncryptedExtension message allows various extensions previously sent in clear in the ServerHello to also enjoy confidentiality protection from active attackers.
Also TLSv1.3 discontinued the support for obsolete ciphers and algorithms. That list includes the following major cryptographic standards/algorithms.
- RC4 Steam Cipher
- RSA Key Transport
- SHA-1 Hash Function
- CBC Mode Ciphers
- MD5 Algorithm
- Various Diffie-Hellman groups
- EXPORT-strength ciphers
- DES
- 3DES
You can read the complete IETF document @ https://tools.ietf.org/html/draft-ietf-tls-tls13-28