For configuring TLS v1.2, the ASA should run software version 9.3(2) or later.
In earlier versions of ASA, TLS 1.2 is not supported.If you are running the old version, it's time to upgrade.
In earlier versions of ASA, TLS 1.2 is not supported.If you are running the old version, it's time to upgrade.
But before that i will show you the config prior to the change. I am running ASA version 9.6.1
Now ,set the server-version to tlsv1.2, though ASA supports version tlsv1.1, its always better to configure the connection to more secure. Server here in the sense, the ASA will be act as the server and the client will connect to the ASA.
#ssl server-version tlsv1.2
set the client-version to tlsv1.2, if required.
#ssl client-version tlsv1.2
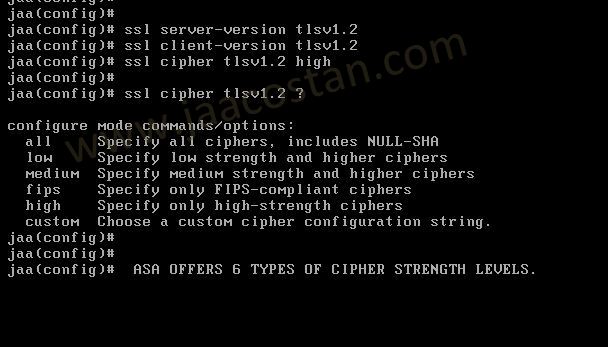
ssl cipher command in ASA offers 5 predefined security levels and an additional custom level.
#ssl cipher tlsv1.2 high
set the client-version to tlsv1.2, if required.
#ssl client-version tlsv1.2
ssl cipher command in ASA offers 5 predefined security levels and an additional custom level.
#ssl cipher tlsv1.2 high
we can see the setting of each cipher levels using #show ssl cipher command.
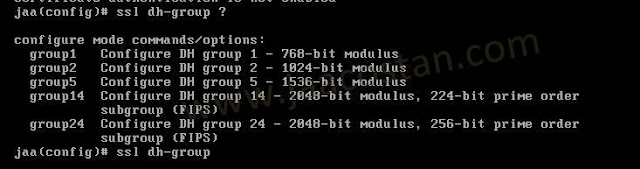
Now set the DH group to 24, which is the strongest offered as of now in the ASA.
#ssl dh-group group24
#ssl dh-group group24
And that it. You can verify it by accessing the ASA/ASDM.
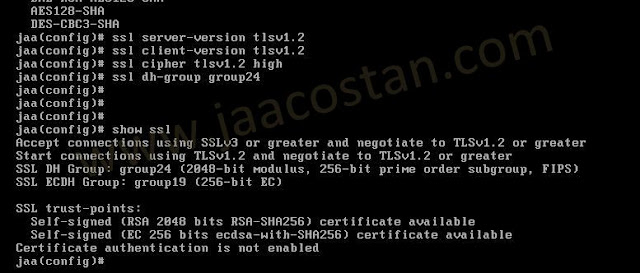
once again check the config using #show ssl command.
You can see the connection will now negotiate to TLSv1.2.
So in Short, just four comments for the configuration.
ssl server-version tlsv1.2
ssl client-version tlsv1.2
ssl cipher tlsv1.2 high
ssl dh-group group24
Note: the same can be done using ASDM .